In this article we will going to learn how to root WP8 Nokia lumia device and inspect internal storage. I am using Nokia Lumia 720 for demo purpose. However Lumia 520, 521, 525, 620, 625, 820, 920, 925, 928, 1020 and 1320 are supported.
XDA developer Heathcliff74 given us powerful tool Windows Phone Internals which allow to unlock the bootloader of selected Lumia Windows Phone models and after unlocking the bootloader, you can enable Root Access on the phone or create and flash Custom ROM's.
The following OS versions Root Access can be enabled. To enable Root Access, the bootloader must be unlocked first.
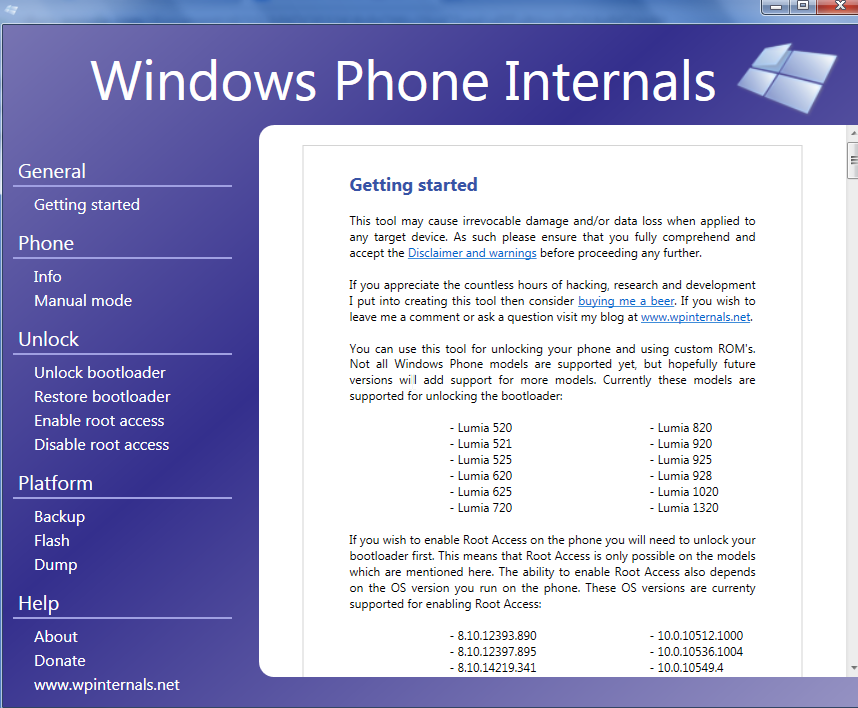
In order to root your device you have to carefully follow the instruction. Download the Windows Phone Internals. The instructions you can find in the tool itself.
I followed instruction for my lumia 720 device only may it's change for your devices, please follow the instruction accordingly.
Before rooting the device we need unlock the bootloader of the device.
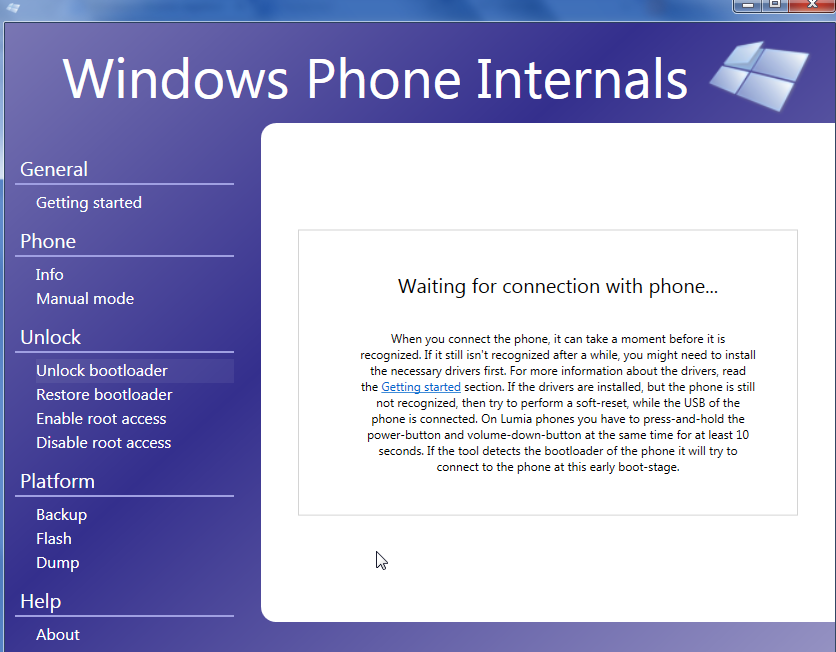
Now Connect you device using USB and unlock your screen. And wait for detection.
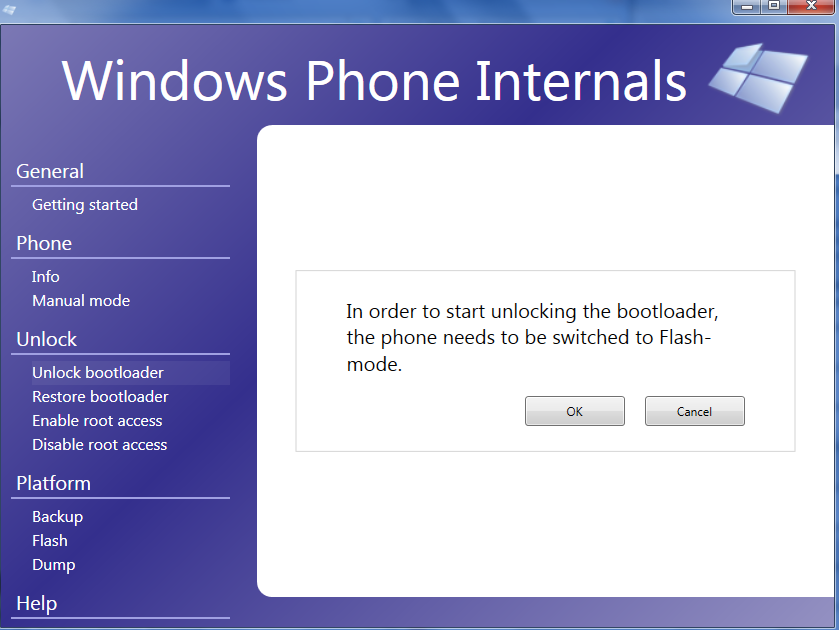
In order to unlock the bootloader of device its ask you to phone needs to be switched to flash-mode. Click on “Ok”
Now we need FFU-image file which is fresh ROM image of your device. It’s important to get the exact same FFU file for your device. To get the FFU file, you need to use Windows Device Recovery Tool which help you to download FFU file for your device. (You need to switch your device in normal mode by Press and hold the Volume Down and Power buttons at the same time until you feel a vibration (about 10-15 seconds). Your phone will restart automatically.)


Now it is very important to use Engineering SBL3 and be careful before using sbl3 file for you device. Make sure that the sbl3 file should work for your device otherwise your device will not work after using wrong sbl3 file.
You can download sbl3 file from xda-developers site for 520, 620, 625, 810, 820, 822, 920, 925 and the 1020.
For me lumia 720 I didn't found sbl3 file but when I research on internet someone posted that lumia 520 sbl3 file will work for lumia 720. So pleae do on your risk.

Now click on continue
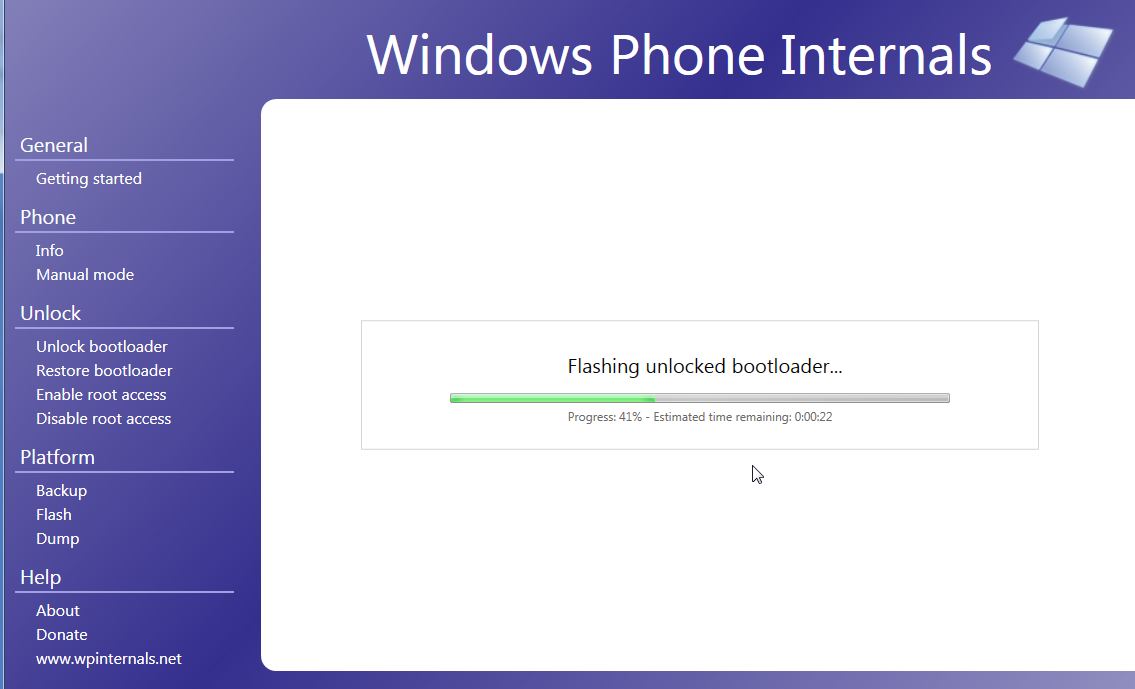
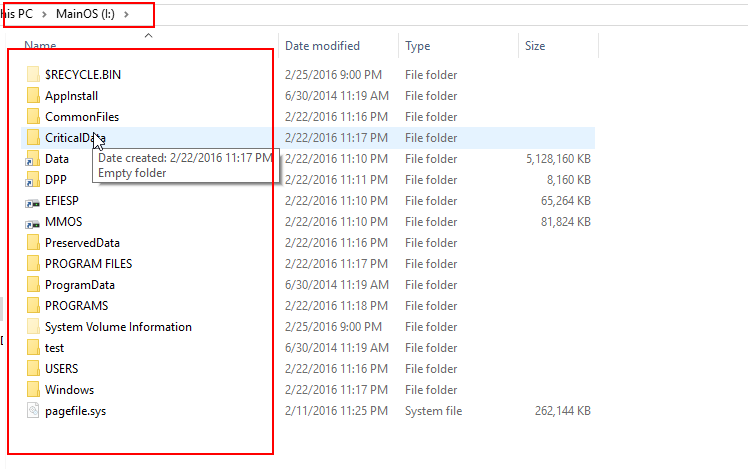
After the booting your device, as your device bootloader has been unlocked. Now move to “Enable Root Access” and click on Unlock Phone. You device will turned into flash mode and switch to Mass Storage mode. In your system you will see drive “MainOS” get active which is your device internal storage.

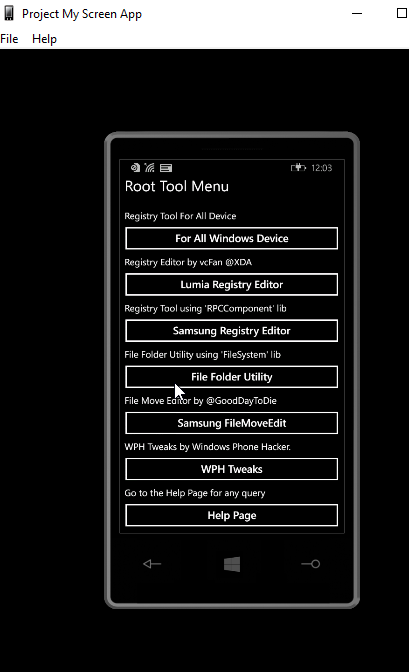
Root tool help you to edit your device registry and provide you to full access on device file system, which can easily access all internal files by only connecting your phone with your system.
Previously Windows phone Internal it give you mass storage mode by flashing your phone, but root tool make your task easier in terms of file access.
Download Root Tool
Now extract the file and Deploy .XAP file into device.
Be careful while using this tool. If you selected any wrong file path or setting may its break your device.
Now select “Lumia Registry Edit”
Go to options >
Now click on Templates
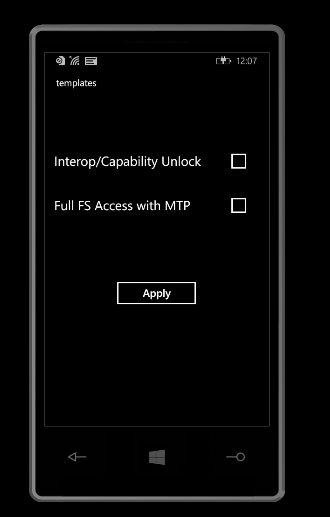
Select both Interop/Capability Unlock and Full FS Access with MTP > Now Apply the setting.

Now you can able to view or edit your device internal storage without switching into flash mode.
There is also cool way to access your device file systems. WP8 Native Access Webserver which provide you to install Client WP8 Native Access .XAP file in your device and by using port you can enable your device into webserver. You can download this app from here.
In this article we learned how we will root our device and inspect internal storage. Next article we will going to learn attack vectors of WP8 application and their vulnerabilities.
XDA developer Heathcliff74 given us powerful tool Windows Phone Internals which allow to unlock the bootloader of selected Lumia Windows Phone models and after unlocking the bootloader, you can enable Root Access on the phone or create and flash Custom ROM's.
OS versions are supported
- 8.10.12393.890
- 8.10.12397.895
- 8.10.14219.341
- 8.10.14226.359
- 8.10.14234.375
- 8.10.15116.125
- 8.10.15148.160
- 10.0.10512.1000
- 10.0.10536.1004
- 10.0.10549.4
- 10.0.10581.0
- 10.0.10586.11
- 10.0.10586.36
In order to root your device you have to carefully follow the instruction. Download the Windows Phone Internals. The instructions you can find in the tool itself.
Fig. 1 Windows Phone Internals
Before rooting the device we need unlock the bootloader of the device.
Fig. 2. Windows Phone Internals Connecting
Now Connect you device using USB and unlock your screen. And wait for detection.
In order to unlock the bootloader of device its ask you to phone needs to be switched to flash-mode. Click on “Ok”
Fig. 3 WP Internals Unlock Bootloader
Now we need FFU-image file which is fresh ROM image of your device. It’s important to get the exact same FFU file for your device. To get the FFU file, you need to use Windows Device Recovery Tool which help you to download FFU file for your device. (You need to switch your device in normal mode by Press and hold the Volume Down and Power buttons at the same time until you feel a vibration (about 10-15 seconds). Your phone will restart automatically.)
Fig. 4 Windows Device Recovery Tool
Now Connect your device and open Windows Recovery Tool, your device will detect after some seconds.
In case you'r getting error while downloading ROM image from Windows Recovery Tool for your device I recommend you to restart your system as well as your device.
Now again switch to Unlock bootloader in windows phone internals.

You should also select a folder where you have Lumia Emergency Flash Loaders. This tool will try to select the Loader that is suitable for your phone.
In case you'r getting error while downloading ROM image from Windows Recovery Tool for your device I recommend you to restart your system as well as your device.
After downloaded the ROM image for your device, the ffu file will be located to path
C:\ProgramData\Microsoft\Packages\Products\RM-885 in your system.
Now again switch to Unlock bootloader in windows phone internals.
Select your .ffu file (Fresh ROM image) which is located at path
C:\ProgramData\Microsoft\Packages\Products\RM-885
Select asC:\ProgramData\Microsoft\Packages\Products\RM-885
Now it is very important to use Engineering SBL3 and be careful before using sbl3 file for you device. Make sure that the sbl3 file should work for your device otherwise your device will not work after using wrong sbl3 file.
You can download sbl3 file from xda-developers site for 520, 620, 625, 810, 820, 822, 920, 925 and the 1020.
For me lumia 720 I didn't found sbl3 file but when I research on internet someone posted that lumia 520 sbl3 file will work for lumia 720. So pleae do on your risk.
Now click on continue
Fig 5. Flashing Unlock bootloader
Fig 6. Enable Root access
Fig 7. Device internal file access.
Root Tool
Root tool help you to edit your device registry and provide you to full access on device file system, which can easily access all internal files by only connecting your phone with your system.
Previously Windows phone Internal it give you mass storage mode by flashing your phone, but root tool make your task easier in terms of file access.
Download Root Tool
Now extract the file and Deploy .XAP file into device.
Fig 8. Root Tool
Be careful while using this tool. If you selected any wrong file path or setting may its break your device.
Now select “Lumia Registry Edit”
Go to options >
Now click on Templates
Select both Interop/Capability Unlock and Full FS Access with MTP > Now Apply the setting.
Now you can able to view or edit your device internal storage without switching into flash mode.